The College of William and Mary’s Information Technology Department recently issued a warning to students, faculty and staff about a recent string of phishing attacks.
According to an email from IT Director of Systems and Support Chris Ward, several students reported they had received phishing emails sent to their school email accounts on May 6. These messages requested that they provide their social security number, address, full name and date of birth. The sender was refundoffice@att.net via cornellcollege.edu.
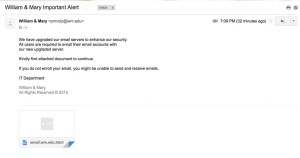
Ward said students should immediately delete and report these emails. People who provided the requested information on the web form should report that to the William and Mary Police Department immediately.
Ward said phishing messages often include misspellings, grammatical errors and links to web pages unaffiliated with the College. He noted that phishing attacks mostly occur on weekends and holidays, when IT departments are closed.
IT Project and Communications Manager Melissa Palacios ’01 M.Ed. ’10 said that the College’s IT department has filters and blocks in place to prevent the majority of phishing messages from reaching users.
“However, hackers are constantly looking for ways to bypass these protections, and occasionally they are successful (these are the phishing messages that actually make it to your Inbox),” Palacios said in an email. “Then, if someone is tricked into providing their WMuserid and password, their account usually gets turned into a “spam bot” spitting out spam and additional phishing message beyond our protections.”
Once the IT department detects unusual activity on an account, it will lock the compromised account until the owner can change their password. However, by that point, the account has usually already sent spam out to other accounts.
Palacios said that the recent attack was particularly successful.
“It pointed people to a screenshot of a familiar OWA email page and stole the credentials of people that attempted to log in to it,” Palacios said. “When the first person fell for it, spam/phishing messages were sent from that person using their @wm.edu account, so the phish appeared to be more authentic.”
The problem quickly escalated as more accounts were compromised, which generated more spam and phishing messages.
“We really don’t have an idea of how many (if any) students might have been compromised by this attack because the student system is operated by Google and you sign-in to the WMApps email using Google login credentials, not your W&M credentials,” Palacios said. “However, we wanted to include students in Thursday’s message to campus as a proactive measure since we could see that spam and phishing messages were being sent to @email.wm.edu addresses.”
IT has determined the location of the machine that sent the original phishing message. According to Palacios, this is not enough information to surmise the attacker’s location or identity.
“There are various layers of compromised machines and proxies that hide the attacker’s true whereabouts and identity,” Palacios said.
A similar phishing attack took place in 2013.